Your password will be hacked – is there anything you can do?
In 2012 LinkedIn, LastFM,and arguably Twitter all had their password databases compromised. 2013 saw Evernote, Facebook and Adobe attacked. And at the begining of 2014 eBay was compromised (although they took their sweet time telling us about it!). Is there anything we can do to protect ourselves? Matt Kirby investigates.
These days we need passwords for everything – from accessing our work PCs, to reading messages on Gmail, to buying things on Amazon. It used to be the case that as long as you avoided easily guessable passwords you’d be fine – unfortunately those days are long gone.
With the growing number of online attacks, hackers now have access to millions of real-world passwords – and they are now using those examples to learn all the clever little tricks that we used to think would protect us – so most of the “password choosing” advice we’ve become used to is no longer applicable.
The vast majority of websites do encrypt our passwords, so when hackers gain access to the database they still have to work hard to decrypt the contents – however with improving software techniques and ever more powerful hardware they are able to crack passwords in days, weeks and months that theoretically would have taken years or lifetimes.
Put simply, if a website holding your password is hacked, there’s a good chance that it’s only a matter of time before your password is known.
What can I do to protect myself?
There are a couple of things you can do to reduce the impact that a password compromise will have, and reduce the likelihood of your password being discovered in the first place.
Do not use a password more than once
If one website is hacked, the attackers will use those known passwords to try to get in to other services. In 2012 some people had their Dropbox accounts logged into by attackers, using details recovered from previous attacks on other websites. If you don’t do anything else, make sure you do this! If you are concerned that your password may have been compromised in one of the recent breaches, you can check here. Enter your email address, and it will tell you if it was in one of the stolen databases.
Use “two-factor” or “two-step” authentication where available
This is using “something you know” (your password) with “something you have” (such as your mobile phone). How it works is that you use a password as usual, but when you login on a new device you also need to enter a one-time code – which is either sent to you via SMS or generated using an app on your phone.
Why is this useful? If a hacker gets hold of your password and attempts to use it, they’ll be prompted to enter the one-time code – which they won’t have. Also, if the two-factor system you are using works via text message you’ll be alerted when someone is trying to login to your account, as you’ll be sent a text.
- Google / Gmail
- Yahoo! Mail
- PayPal
- Dropbox
- Microsoft
- Apple ID / iCloud
- Evernote
- Tumblr
- LastPass
There is an extensive list available at TwoFactorAuth.org
Use a “password manager”
Systems like LastPass, KeePass or 1Password can create long, random passwords that you can use for each website, and some systems will even automatically log you in each time. It’s all secured by one master password – so you only need to remember one password to access your personal database of unique passwords.
In our opinion the best of the above services is LastPass. They also support two-factor authentication as an additional security measure, and will alert you if your details are included in a future database leak.
The LastPass basic service is free, however their “Premium” option (which includes their mobile apps) is only $12 (approx £7.65) per year – which is a small price to pay for increased security and piece of mind.
Choose a better password
If you are unable to use a password manager (you use multiple devices, or you regularly use systems where you can’t install software – although LastPass has options for this), you need to make sure that your password is as secure as it can be, while continuing to be usable.
Even if you do use a password manger, you still need a way to create a master password that’s easy for you to use, but offers sufficient security.
How to choose a better password
Given that a hacker with a stolen password database, the right software and hardware, and some time on their hands will eventually get to your password, what’s the best that you can do to delay this as long as possible?
Firstly, ignore all other advice you’ve previously heard about how to choose a password – those methods don’t cut it any more. Also don’t bother with any “password strength” testers – these have not been updated to reflect the current threats. As an example, the website How Secure Is My Password? estimates it would take a million years to crack “Sup3rThinkers”, however in 2012 this password was cracked in a matter of months.
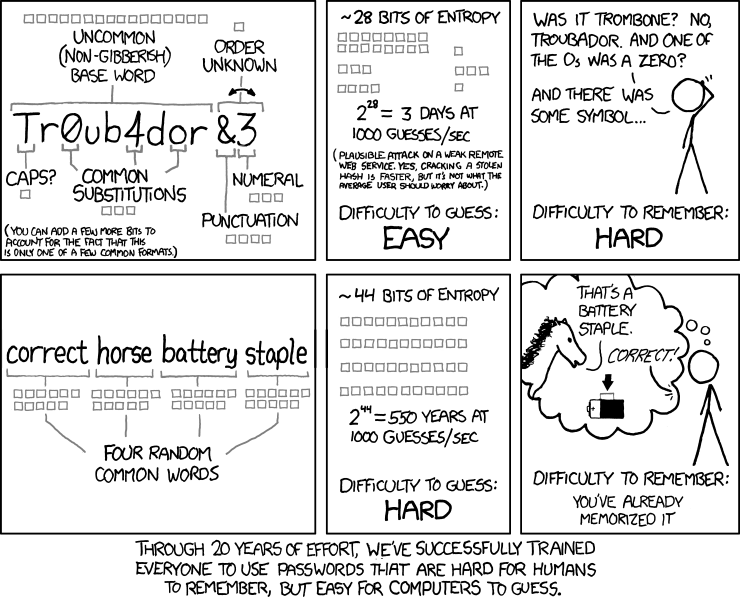
Below is a system that will give you a password that is a balance between usability and security. You’ll end up with a long password that should be easy to remember, while providing a reasonable amount of protection against it being cracked. Do note that this won’t give you the most secure password possible (a long string of random characters is better), but if a hacker does attempt to decrypt a password database this password won’t be one of the first to fall.
This method is now recommended by the Home Office under their “Cyber Street Wise” campaign.
How to do it
- Think of at least 3 or 4 random, unconnected, words. Do not pick words that often appear together, and definitely do not use phrases. If you need help, try this random word generator.
- To make it more secure than the example below, add complexity: add capitals, numbers and symbols / punctuation. Try to add things into words, not just at the beginning or end
This comic from XKCD gives an example:
Things to note
- This example is just a starting point – words on their own are not secure enough
- Make the words as random as possible – even to the point of making up some words, or deliberately misspelling some words
- If you can, use some non-English words
- When adding complexity avoid just putting things at the start or end of words
Creating variations for different services
Ideally you’d use the above method to create totally unique passwords for each service you use – but you then have the problem of remembering which password is for which service, which would cause you to write this down, at which point you might as well use a password-manager anyway.
It’s far easier to pick one password and extend it by by inserting another word that you associate with the service you are logging in to. That way the password for each system is different, but all are based on a common starting point.
A couple of examples
- For Gmail you could use something like “letters”, “communication” or “spam”
- For Facebook it could be something like “friends”, “fun” or “skiving”
- When you have chosen your word, add capitals, numbers and punctuation, and insert it into your base password (don’t just stick it on the end)
When picking a word that you associate with a particular service, try to think what a hacker would presume if they did see your password. If its too obvious how you chose the word, they’ll be able to use the same logic to guess what word you picked for another service. Obviously anything based on the website’s name would make it far too easy for a hacker.
The future?
Ultimately websites need to use more secure methods for storing our details – encryption alone is no longer secure enough. Websites should be “salting” our passwords when encrypting them – this is taking our password, adding another password known only to them, and then encrypting the whole lot. This makes many cracking attacks impractical, and will vastly increase the amount of computing power and time needed to do so.
In March 2013 when Evernote was hacked they went public quickly and forced everyone to change their passwords. However, this was only a (very wise!) precaution, as Evernote were salting their passwords so it would be highly unlikely that anyone would ever be able to retrieve them – but if they did they would then be useless as they had all been changed in the interim.
Personally I think that more services need to start offering two-factor authentication, as that is far more secure than passwords alone. Longer-term I think we will all move away from using passwords anyway as they are becoming increasingly weak as a security measure, and we are all needing to secure access to more and more systems. Biometrics may be the future, however we have a long way to go before we can rely on their security.
A newly proposed system called SQRL (pronounced “squirrel”) could also be a good replacement for passwords, if it gains enough traction and becomes widely available. This system dispenses with usernames and passwords in their entirety – to login to a website you either scan a QR code, or click a link.
In the meantime all we can do is make our passwords as secure as practical, change our passwords when a service is compromised, and put our faith into the security practices of our most used webservices.
Further Reading
This article on Ars Technica gives a detailed technical explanation of how current hackers are able to crack passwords that were previously thought close to invincible.
Tags: better password hacking password manager passwords security two-factor authentication

0 Comments on "Your password will be hacked – is there anything you can do?"